My software, QuickDAV, is not in the AUR. It’s open source, and I release it only as an AppImage, because I am lazy.
I’m Hunter Perrin. I’m a software engineer.
I wrote an email service: https://port87.com
I write free software: https://github.com/sciactive
- 2 Posts
- 76 Comments
The Firefox snap was the reason I left Ubuntu. (Or, the last straw, at least.) Fedora has been wonderful.
Ultimately, you can’t. Even if everything you’re doing is encrypted, they have access to the RAM that’s holding your encryption keys.

 2·7 days ago
2·7 days agoIf you want cheap encrypted storage you can run a Nephele server with encryption and something like Backblaze B2.

 4·9 days ago
4·9 days agoYes, that’s why degloogled Android is best. It doesn’t matter if you use privacy centric apps if your OS is spying on you.

 19·9 days ago
19·9 days agoI see a lot of people in here shitting on iOS and not Google. Stock Android is worse than iOS for privacy. Unless you’re going to run a degoogled Android, don’t bother getting rid of iOS. But degoogled Android is the best option, if you can.
It’s not completely FOSS, but I run Port87, which is quite a bit FOSS. It uses Haraka as its SMTP server, SvelteKit as its server framework, Nymph.js as its database layer, Svelte as its frontend framework, and Svelte Material UI as its UI framework.
The ones that I created and maintain are:
The base app layout is also available on GitHub.
You can try them both and see which one you like. Gnome is great, and it’s my preference, but KDE is also great.

 1·13 days ago
1·13 days agodeleted by creator

 3·16 days ago
3·16 days agoThe way I’ve done it is Ubuntu Server with a bunch of Docker Compose stacks for each service I run. Then they all get their own subdomain which all runs through the Nginx Proxy Manager service to forward to the right port. The Portainer service lets me inspect things and poke around, but I don’t manage anything through it. I want it all to be super portable, so if Ubuntu Server becomes too annoying, I can pack it all up and plop it into something like Fedora Server.

 2·16 days ago
2·16 days agoThey can’t do 4K video. The best they can do is 1080p30.

 1·17 days ago
1·17 days agoI didn’t say Raspberry Pi Zero. Those are niche machines. They’re not fast enough to do general purpose computing.

 1·17 days ago
1·17 days ago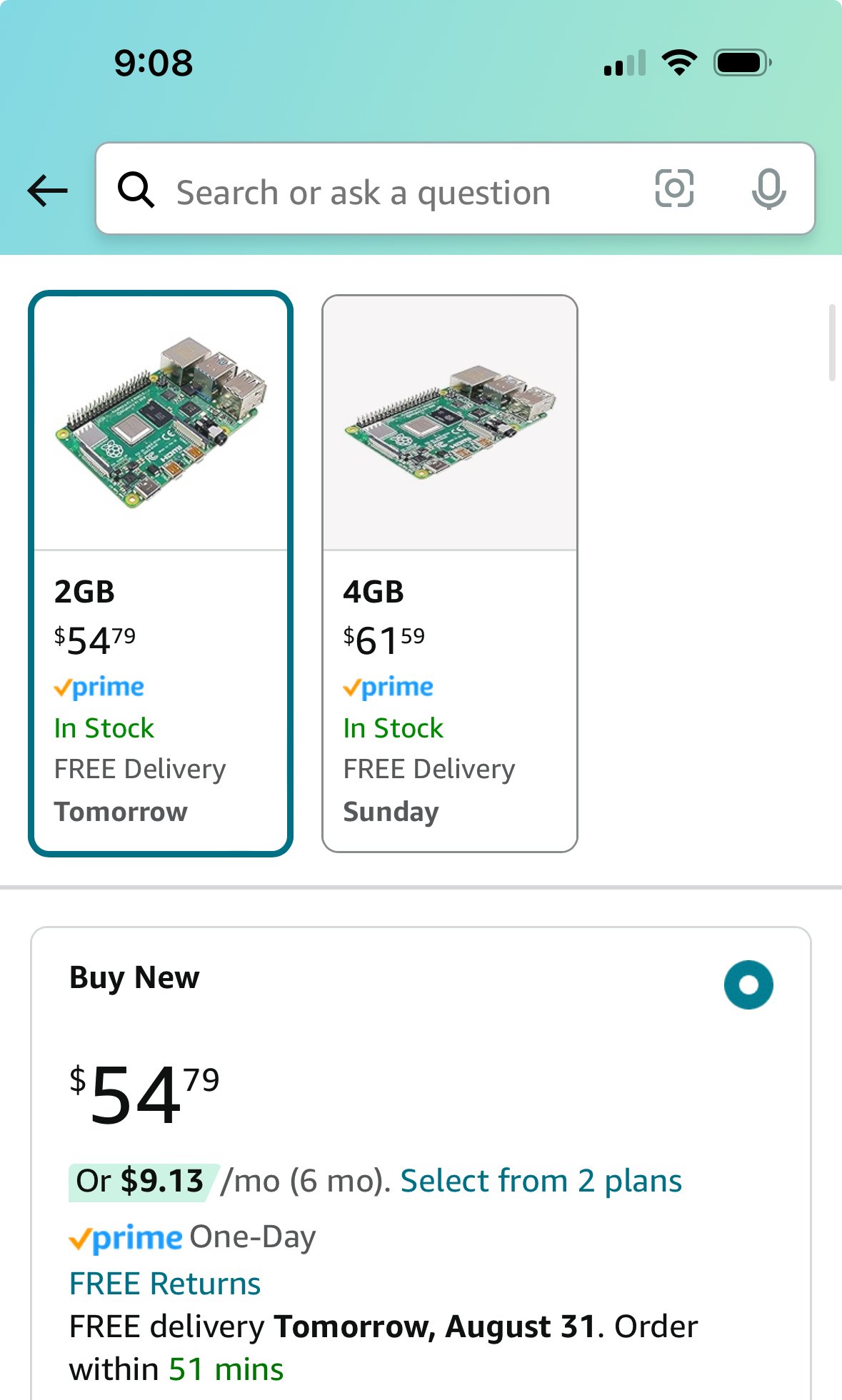
2.4 times. But, who’s counting?

 1·18 days ago
1·18 days agoNo. They emulate a keyboard, and use the keyboard shortcuts to do things in Windows. So they won’t work out of the box in Linux, but you can add each of the keys as a keyboard shortcut, then they’ll work.

 1·18 days ago
1·18 days agoI’d recommend the Pepper Jobs windows 10 gyro remote. I’ve got two of them because they’re so great.

 1·18 days ago
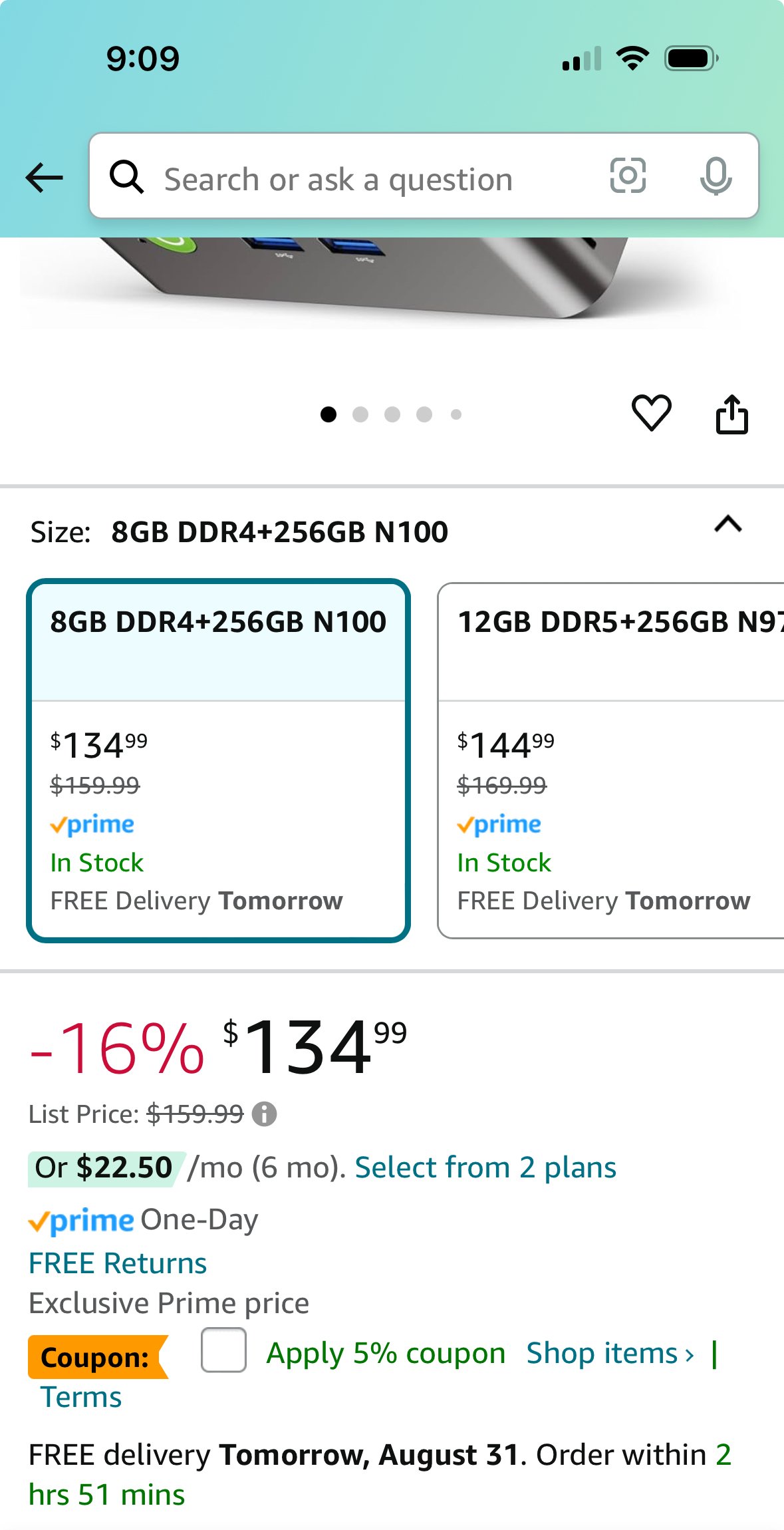
1·18 days agoExactly. N100 mini PCs are like the Swiss Army Knife of computers. Almost as compact as a Raspberry Pi, and compatible with a lot more things.

 2·21 days ago
2·21 days agoShadowsocks doesn’t look anything like HTTPS traffic. It looks like a bare stream cipher over TCP connections to one host with bursts of traffic. HTTPS starts off with a TLS handshake (a client hello, a server hello, the server certificate, then a cipher negotiation and key exchange) before any ciphertext is exchanged. Shadowsocks just starts blasting a ciphertext stream. Even if you run it on port 443, it looks nothing like HTTPS.
Without any sort of cipher negotiation and key exchange, it’s obvious that it’s a stream cipher with a pre shared key, so this would be automatically suspicious. There’s also not really any plausible deniability here. If they probe your Shadowsocks host and see it running there, that’s all the proof they need that you’re breaking their rules. With a VPN, you could at least say it’s for a project, and with SSH, you could say you’re just transferring files to your own machine.

 1·21 days ago
1·21 days agoI mean, they could have used their eyeballs, but we don’t know, because he didn’t say.
Shadowsocks would work, but I feel like bare stream ciphers over TCP are a dead giveaway that you’re bypassing content restrictions. Especially if they probe that host and see it running. But, what do I know? It’s just my job five days a week.

 1·22 days ago
1·22 days agoIt very much is. I used it regularly in both high school and college. In high school it was just how I connected to other machines. One of my teachers taught me how to use it. In college we were told to use it by the professor, so at least one entire class was using it for every assignment. That’s pretty normal in any school that has programming or networking courses.
SSH is usually used for work, so it just looks like someone working. Tor is used for nefarious purposes, so it will always look suspicious. VPNs are used to bypass content restrictions, so they will always look suspicious.



Ouch. xD
It’s super easy to create. And you distribute it on your own, so it’s basically like an installer exe on Windows. In my mind it’s one step above only offering source code.